This 4-week course offers online sessions twice weekly, focusing on risk management in cybersecurity. Topics include Risk Analysis, Risk Management Lifecycle, and practical application techniques in managing cybersecurity risks. Delivered by Rafeeq Rehman at SISARGO Institute, it’s tailored for professionals seeking to advance in risk management.
Release Notes April 28, 2024
Following are release notes for April 28, 2024. This release includes minor updates that creates a sorted list of findings when displaying an assessment.
While risk assessment may be qualitative, quantitative, estimating “control strength” is an important part of calculating overall risk (especially in qualitative and quantitative methods). To improve consistency and to decrease subjectivity in estimating control strength, I am providing some examples of how to estimate control strength in this article.
Defense in depth is a fundamental concept in Cybersecurity. This strategy involves layering multiple security measures to protect against various threats. Imagine a series of concentric circles, each representing a layer of defense, with the innermost circle being the most critical and the outer layers providing additional security.
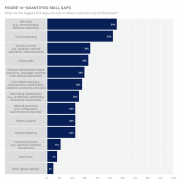
ISACA published a report on “State of Cybersecurity 2022” in which they presented their findings on the global workforce. The most striking of all the findings is Figure 14 of the report showing major skill gaps among security professionals.